

Taiyo Kogyo Column
Mechanism to prevent image tampering│Electronic blackboards for business efficiency
2017.05.26

現場の進捗や出来栄えを確認するための写真台帳。
現在も手書きのチョーク書き黒板を用いての撮影が主流ですが、最近では電子黒板が普及し始めています。でも「電子黒板のメリットは分かっていても実際の利用に不安がある」といった声がよく聞かれます。あるいは「関係者の意向で使えない」なんていう事情もあるかもしれません。
電子黒板の一般的普及にはいくつか課題がありますが、そのうちの一つが”画像の改ざん”ではないでしょうか。電子黒板=画像の編集というイメージも少なからずあると思います。
今回は、国交省でも利用されている電子黒板のメリットと、画像の改ざんではないことを証明する仕組みについてご紹介します。この記事を読んだ後には、電子黒板への不安はなくなるはずです。
電子黒板を使いこなして写真台帳を自動作成できれば作業が一層楽になります。
Advantages of Electronic Blackboards
Compared to the traditional handwritten blackboard, the electronic blackboard has several advantages.
- A single person can take field photographs.
- Eliminates the need to bring blackboards into tight spaces or dangerous heights.
- It saves the time of typing the same information as on the blackboard twice in the photo ledger.
特に台帳の写真右側に記入する文章はほとんどの場合、黒板に記載した内容と同じです。黒板にも文章を書いて、写真撮影後に台帳にも同じ文章を入力するのは二度手間です。
黒板に記入した内容が自動で台帳に転記されれば、作業はとっても簡単になります(もちろん変更が必要な写真は修整が必要になりますが)。
電子黒板を使って台帳を自動作成するツールは世の中に相当数出ていることもあり、使い方をマスターするのはそう難しくないと思います。

In most cases, the text in the photo ledger is the same as the content on the blackboard.
That's why I'm worried about electronic blackboards.
一方で「電子黒板=画像の編集」というイメージを持たれる方も多いかと思います。公共工事で提出する写真台帳は、画像の加工が一切認められておらず、それもあって電子黒板そのものが画像の編集にあたるのではないかという疑問が出てくるということです。

また電子黒板の場合、一見しただけでは「画像を後から編集しているのではないか?」といった疑問の余地が残るため、提出先に敬遠されるケースもあると聞きます。そういった疑問や指摘を受けたときに画像を編集していないことを証明する手段がなければ、結局は電子黒板は使えないということになります。
電子黒板への文字入力が慣れないことも重なり、電子黒板の利用に踏み切れない方も多いのではないでしょうか。
What is image tampering protection?
In February of this year, the Ministry of Land, Infrastructure, Transport and Tourism began allowing the use of electronic blackboards in construction projects under its direct control. For a long period of time up to that point, a major challenge was to prove that “images created using electronic blackboards have not been tampered with.
In response to this challenge, in February 2017, specifications were determined based on specific technical standards, and a system for detecting image tampering was established. These technical standards are publicly available*1 and a checking tool to detect image tampering is also available from JACIC*2*3.
In response to this technology, software with a tamper-proof mechanism (i.e., software with electronic blackboard functions that can be used for construction projects directly under the Ministry of Land, Infrastructure, Transport and Tourism) is also listed* 4 is available on the website.
1 “e-Government Recommended Cipher List” (https://www.cryptrec.go.jp/list.html)
*2 “Check System (Authenticity Check Tool)” ( https://dcpadv.jacic.or.jp/photofinder/pac_auth.php) *3 JACIC: Japan Construction Information Center
*3 JACIC: Japan Construction Information Center
*4 “Software for digitizing small blackboard information of digital construction photos” (https://www.cals.jacic.or.jp/CIM/sharing/pdf/software %EF%BD%882904.pdf )
具体的に「改ざん防止を証明する機能」とはどのような仕組みでしょうか。
jpeg等の画像ファイルには、画像データを格納する領域と、”撮影日”や”撮影場所(GEOコードなど)”等のメタ情報と呼ばれる付属データを格納する領域の2つが存在します。
画像の改ざんも2種類考えられ、一つは画像をペイント等のソフトで加工して画像データを編集するものです。もう一つはメタ情報を変更するもので、やり方によっては履歴を残さず撮影日などを変更することができます。(画像上の)電子黒板の撮影日を書き換えて過去の写真を現在撮影したかのように用いるのは、前者の改ざん方法となります。
JPEGのメタ情報「撮影日」。やり方によっては変更できる。
The JACIC, which is commissioned by the Ministry of Land, Infrastructure, Transport and Tourism to conduct research on electronic blackboards, uses a formula called a “hash function” to deal with this kind of image file tampering. A hash function replaces data with a fixed-length value (in this case, a numerical value for simplicity) using a certain formula, and the replaced value is called a “hash value. Since it is impossible to recover the original data from a hash value and the probability of generating the same hash value from different files is astronomically small, hash functions are widely used for tamper detection and file identity verification.

Generate a "hash value" when construction photos are taken to ensure tamper-resistance
Software with tamper-resistant mechanisms can be described, metaphorically speaking, as creating a keyhole to verify tampering. The key is re-made at the time of checking and verified by whether the key fits or not. If the key fits, it is considered OK. If the key does not fit, we leave aside whether it was intentional or not and judge that there was tampering. This keyhole is automatically created immediately after the picture is taken.
Easy tampering check
We have explained that the system for detecting image tampering is based on a “hash function. Tools with this checking function can be downloaded free of charge from the website of the Japan Construction Information Center ( JACIC) (JACIC website ).
There are also other tools for electronic delivery and photo organization that have this checking function ( Software List ).
It should be noted that jpeg files taken with other than compatible software cannot be checked. The hash value must be stored under lock and key, so the hash value will only be stored if the image was taken with a tool that has this key and formula.
In other words, the image cannot be checked unless it was taken with software that supports the tamper-detection mechanism, and proof of image tamper-resistance is not possible.
In fact, an image taken with software (device) that does not support the tamper detection mechanism is subjected to the JACIC (Digital Construction Photograph Authenticity Check) check tool. The result was determined to be a “file not subject to check”.
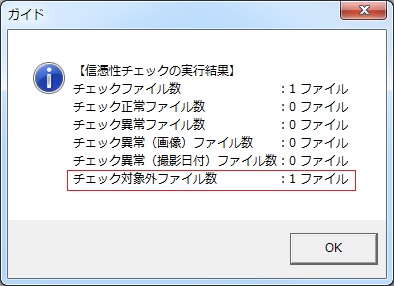
Images not taken with compatible software are judged as "not subject to check".
The “Mirai Construction 2” mobile application, which allows users to take construction photos for free, supports a tamper detection system.
Let’s run a check tool on a photo taken with “Mirai Construction 2” and a processed version of the photo. The operation is quite simple; just select the images you want to check and press the Run button.
The results of the check are displayed in a dialog box, and in this case, they are sorted into “normal” and “abnormal” files. A CSV file summarizing the results is also output, so you can check at a glance which files were NG.
Operation of the check tool is simple. Simply select an image and run the check.
Electronic blackboards that can be used from tomorrow
We hope you have enjoyed this brief introduction to the tamper-evident mechanism. If you understand the existence and mechanism of the checking tool, there is no need to worry about the use of electronic blackboards. Also, as you may have noticed, this tamper-proof mechanism is not directly related to the electronic blackboard. It is only a mechanism to prove “that the electronic blackboard is not a processing of images,” and the tamper-evident check mechanism also applies to photos taken with a conventional chalk-writing blackboard.
Mirai Construction 2, a free application that automatically creates photo ledgers, includes a tamper-proof function in both the electronic blackboard and chalkboard photo mode. In addition, electronic blackboards require time-consuming input, but “Mirai Construction 2” has a history function. Mirai Construction 2 has a history function, which automatically records what has been entered so far and displays predictions. The more you use it, the easier the work becomes. For more information on “Mirai Construction 2,” see “[Free Ledger Application! See also “Free Photo Ledger App for Construction Work” for more information on Mirai Construction 2. Please try out Mirai Construction 2 for the ultimate in time-saving, efficient photo ledger operations.


https://www.miraikoji2.com
Log in to the web version of “Mirai Construction 2”
https://www.miraikoji2.com/users/sign_in
Construction Businessへの
Contact us
- TOP>
- Taiyo Kogyo Column>
- Mechanism to prevent image tampering│Electronic blackboards for business efficiency





